Coaxial cable consists of a hollow outer cylindrical conductor that surrounds a
single inner wire made of two conducting elements. One of these elements,
located in the center of the cable, is a copper conductor. Surrounding the
copper conductor is a layer of flexible insulation. Over this insulating
material is a woven copper braid or metallic foil that acts both as the second
wire in the circuit and as a shield for the inner conductor. This second layer,
or shield, can help reduce the amount of outside interference. Covering this
shield is the cable jacket (See Figure 1.1)
Figure 1.1 Coaxial Cable (
Coaxial cable supports 10 to 100 Mbps and is
relatively inexpensive, although it is more costly than UTP on a per-unit
length. However, coaxial cable can be cheaper for a physical bus topology
because less cable will be needed. Coaxial cable can be cabled over longer
distances than twisted-pair cable. For example, Ethernet can run approximately
100 meters (328 feet) using twisted-pair cabling. Using coaxial cable increases
this distance to 500m (1640.4 feet). For LANs, coaxial cable offers several
advantages. It can be run with fewer boosts from repeaters for longer distances
between network nodes than either STP or UTP cable. Repeaters regenerate the
signals in a network so that they can cover greater distances. Coaxial cable is
less expensive than fiber-optic cable, and the technology is well known; it has
been used for many years for all types of data communication.
When working with cable, you need to consider
its size. As the thickness, or diameter, of the cable increases, so does the
difficulty in working with it. Many times cable must be pulled through existing
conduits and troughs that are limited in size. Coaxial cable comes in a variety
of sizes. The largest diameter (1 centimeter [cm]) was specified for use as
Ethernet backbone cable because historically it had greater transmission length
and noise-rejection characteristics. This type of coaxial cable is frequently
referred to as Thicknet. As its nickname suggests, Thicknet cable can be
too rigid to install easily in some situations because of its thickness. The general
rule is that the more difficult the network medium is to install, the more
expensive it is to install. Coaxial cable is more expensive to install than
twisted-pair cable. Thicknet cable is almost never used except for
special-purpose installations. A connection device known as a vampire tap was
used to connect network devices to Thicknet. The vampire tap then was connected
to the computers via a more flexible cable called the attachment unit interface (AUI). Although this
15-pin cable was still thick and tricky to terminate, it was much easier to
work with than Thicknet. In the past, coaxial cable with an outside diameter of
only 0.35 cm (sometimes referred to as Thinnet) was used in Ethernet
networks. Thinnet was especially useful for cable installations that required
the cable to make many twists and turns. Because it was easier to install, it
was also cheaper to install. Thus, it was sometimes referred to as Cheapernet.
However, because the outer copper or metallic braid in coaxial cable comprises
half the electrical circuit, special care had to be taken to ensure that it was
properly grounded. Grounding was done by ensuring that a solid electrical
connection existed at both ends of the cable. Frequently, however, installers failed
to properly ground the cable. As a result, poor shield connection was one of
the biggest sources of connection problems in the installation of coaxial
cable. Connection problems resulted in electrical noise, which interfered with
signal transmittal on the networking medium. For this reason, despite its small
diameter, Thinnet no longer is commonly used in Ethernet networks.
The most common connectors used with Thinnet are
BNC, short for British Naval Connector or Bayonet Neill Concelman, connectors (see
Figure 8-5). The basic BNC connector is a male type mounted at each end of a
cable. This connector has a center pin connected to the center cable conductor
and a metal tube connected to the outer cable shield. A rotating ring outside
the tube locks the cable to any female connector. BNC T-connectors are female
devices for connecting two cables to a network interface card (NIC). A BNC
barrel connector facilitates connecting two cables together.
Figure 1.2 Thinnet and BNC Connector
The following summarizes the features of coaxial cables:
• Speed and throughput—10 to 100 Mbps
• Average cost per node—Inexpensive
• Media and connector size—Medium
• Maximum cable length—500 m (medium)
Plenum Cable
Plenum cable is the cable that runs in plenum
spaces of a building. In building construction, a plenum (pronounced PLEH-nuhm,
from Latin meaning “full”) is a separate space provided for air circulation for
heating, ventilation, and air-conditioning (sometimes referred to as HVAC), typically
in the space between the structural ceiling and a drop-down ceiling. In
buildings with computer installations, the plenum space often is used to house
connecting communication cables. Because ordinary cable introduces a toxic hazard
in the event of fire, special plenum cabling is required in plenum areas. In
the United States, typical plenum cable sizes are AWG sizes 22 and 24. Plenum
cabling often is made of Teflon and is more expensive than ordinary cabling.
Its outer material is more resistant to flames and, when burning, produces less
smoke than ordinary cabling. Both twisted pair and coaxial cable are made in
plenum cable versions.
Fiber-Optic Cable
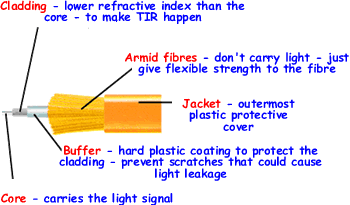
Fiber-optic cable used for networking consists of two fibers encased
in separate sheaths. If you were viewing it in a cross-section, you would see
that each optical fiber is surrounded by layers of protective buffer material,
usually a plastic shield, then a plastic such as Kevlar, and finally an outer
jacket. The outer jacket provides protection for the entire cable, while the
plastic conforms to appropriate fire and building codes. The Kevlar furnishes
additional cushioning and protection for the fragile, hair-thin glass fibers
(see Figure 8-6). Wherever buried fiber-optic cables are required by codes, a
stainless-steel wire sometimes is included for added strength.
Figure 1.3 Fiber-Optic Cable
Figure 1.4 Fiber-Optic Cable
The light-guiding parts of an optical fiber are called the core
and the cladding. The core is usually very pure glass with a high
index of refraction. When a cladding layer of glass or plastic with a low index
of refraction surrounds the core glass, light can be trapped in the fiber core.
This process is called total internal reflection. It allows the optical fiber
to act like a light pipe, guiding light for tremendous distances, even around
bends. Fiber-optic cable is the most expensive but it supports line speeds of more than 1 Gbps.
Two types of fiber-optic cable exist:
• Single-mode—Single-mode
fiber cable allows only one mode (or wavelength) of light to propagate through
the fiber. It is capable of higher bandwidth and greater distances than multimode,
and it is often used for campus backbones. This type of fiber uses lasers as
the light-generating method. Single-mode cable is much more expensive than
multimode cable. Its maximum cable length is more than 10 km (32808.4 feet).
Figure 1.4 Fiber-Optic Cable
• Multimode—Multimode
fiber cable allows multiple modes of light to propagate through the fiber. It
is often used for workgroup applications and intrabuilding applications such as
risers. It uses light-emitting diodes (LEDs) as a light-generating device. The
maximum cable length is 2 km (6561.7 feet). The characteristics of the
different transport media have a significant impact on the speed of data
transfer. Fiber-optic cable is a networking medium capable of conducting
modulated light transmissions. Compared to other networking media, it is more
expensive. However, it is not susceptible to EMI, and it is capable of higher
data rates than any of the other types of networking media discussed in this
chapter. Fiber-optic cable does not carry electrical impulses as other forms of
networking media that use copper wire do. Instead, signals that represent bits are
converted into beams of light.
NOTE- Even
though light is an electromagnetic wave, light in fibers is not considered
wireless because the electromagnetic waves are guided in the optical fiber. The
term wireless is reserved for radiated, or unguided, electromagnetic
waves.
Fiber-optic connectors come in single-mode and multimode varieties.
The greatest difference between single-mode connectors and multimode connectors
is the precision in the manufacturing process. The hole in the single-mode
connector is slightly smaller than in the multimode connector. This ensures
tighter tolerances in the assembly of the connector. The tighter tolerances
make field assembly slightly more difficult. A number of different types of
fiber-optic connectors are used in the communications industry. The following
list briefly describes two of the commonly used connectors:
• SC—SC type connectors feature a push-pull connect
and disconnect method. To make a connection, the connector is simply pushed
into the receptacle. To disconnect, the connector is simply pulled out.
• ST—ST fiber-optic connector is a bayonet type of
connector. The connector is fully inserted into the receptacle and is then
twisted in a clockwise direction to lock it into place.
Figure 8-7 ST Fiber-Optic Connector
The following summarizes the features of fiber-optic cables:
• Speed and throughput —More than 1 Gbps
• Average cost per node —Expensive
• Media and connector size—Small
• Maximum cable length —More than 10 km for single
mode; up to 2 km for multimode








.jpeg)






